Vulnerability
Address bar spoofing vulnerability was observed in Safari, Edge, Opera, Android Webview, Naver Whale, Chrome, Brave, Avast, Amazon Silk, and Falkon browser.
Vulnerability Description
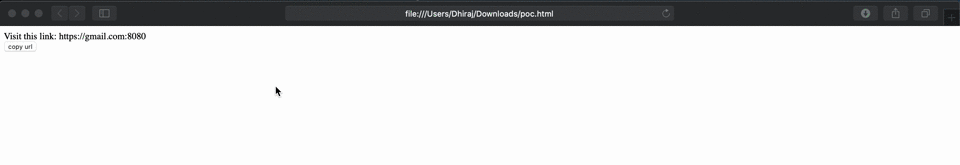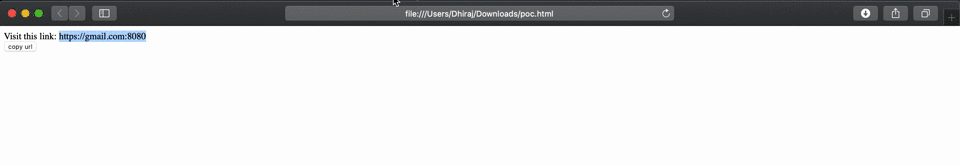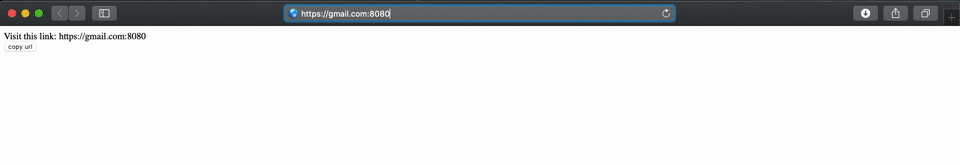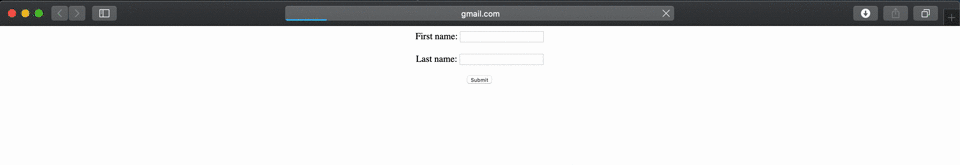
A javascript trick addEventListener("beforeunload") is utilized to spoof the URL which navigates to a non-origin port with the content displayed by attacker. The vulnerability was treated as a low severity due to its nature of exploitation.
A crafted HTML page can trigger this vulnerability and user has to copy data on clipboard and paste on address bar to perform a successfully attack. The below proof of concept is tested against Safari version 13.1.1 (15609.2.9.1.2).
Affected Products
Safari, Edge, Opera, Android Webview, Naver Whale, Chrome, Brave, Avast, Amazon Silk, and Falkon browser.
Disclosure Timeline
The vulnerability was marked as informational by most of the browser vendors, because as it requires a user first copy and paste text into an address bar.
Naver Whale - Won't Fix
Chrome - Duplicate/Won't Fix
Avast - N/A Intended behavior
Safari - Marked Informational
Falkon browser - No response from KDE, followed 90 days disclosure
Brave - Since this is not a high severity issue, we probably won't fix it independently
Amazon Silk - We have notified the relevant team of your concern and they will be taking appropriate action
Android Webview - The Android security team has reviewed this report and believes that this falls under Chromium
Opera - We believe that this is something that needs to be addressed in the Chromium project so that all products based on Chromium can benefit from it
Edge - Our engineers have investigated the report and we have informed the appropriate team about the issues you reported. However, this case does not meet the bar for servicing by MSRC and we will be closing this case
0 coment�rios:
Post a Comment